Penetration tests (security assessment) are controlled attacks on the resources of the organization or its individual components Penetration testing is a form of ethical hacking – it’s an intentional attempt of simulated cyberattacks performed by penetration testers using strategies and specialized tools designed to access or exploit computer systems, networks, websites, and applications. Pentests allow to see the actual level of information security – identification of risks, which may be targeted and effectively hacked. It can examine whether a system is robust enough to withstand attacks from authenticated and unauthenticated positions, organization’s regulatory compliance, its employees' security awareness, and the organization's ability to identify and respond to security issues as well as a range of system roles.
SC2labs offers professional penetration testing on any of the company’s IT infrastructure.
Depending on your needs we offer :
- Web application and API penetration tests
- Mobile application penetration tests
- PCI Penetration tests
- Internal and External Penetration service
- Black-box type – from the perspective of a zero-knowledge test systems
- Gray-box type – partial knowledge of the test system
- White-box type – the full knowledge of the test system
Web Application and API Security Assessment: exclusively focused on vulnerability/bug discovery that might be exploited using web application or API WebService provided functionalities, supported business models and information flows. To perform Web Application Audit, we are using industry proven methodologies and best practices like OWASP ASVS and NIST Special Publication 800-95: Guide to Secure Web Services.
To deliver security assessment, testers combine dynamic testing and manual analysis, assisted by specific tools:
- Manual (dynamic) security analysis against the software
- Automated (dynamic) security analysis of the software
- Automated static code security analysis (Java Script / Client Side)
Software Security Inspections where security testers manually review if security requirements are accomplished:
Manual review/security inspection on requested security functionalities
Manual review/security inspection on requested security architecture
Security inspection on software device-server communications/data flows /web services
Security inspection on authentication and authorization mechanisms
Security Inspections of data generated and stored by a native mobile application (logs, reports) versus protection of data and user privacy
Security checks on business logic, making use of implemented functionalities and looking for misuse scenarios in front of:
- User impersonation
- Elevation of privileges
- Users’ privacy breaches
- Unauthorized access
- Critical parameter manipulation & access to unauthorized information/content
- Business constraint exploitation
- File or unauthorized URL access & business information extraction
- Other potential applicable attacks to the tested mobile application and corresponding API.
These standards together with our in-depth experience in the security area allow us to examine tested environments and provide clear business and technological recommendations of how to bring your applications security to a higher level, eliminating threats caused by security vulnerabilities.
A PCI Pentest is a pentest that has specific requirements under PCI DSS to verify the protection of Cardholder Data. PCI DSS penetration testing is designed to include the assessment of network infrastructure and applications from both outside and inside an organisation’s network environment.
PCI DSS Requirements 11.4.1 and 11.4.2 state that internal and external penetration testing must be performed at least annually and after any significant changes – for example, infrastructure or application upgrades or modifications, or after installing new system components. Requirement 11.4.5 requires penetration testing of network segmentation controls.
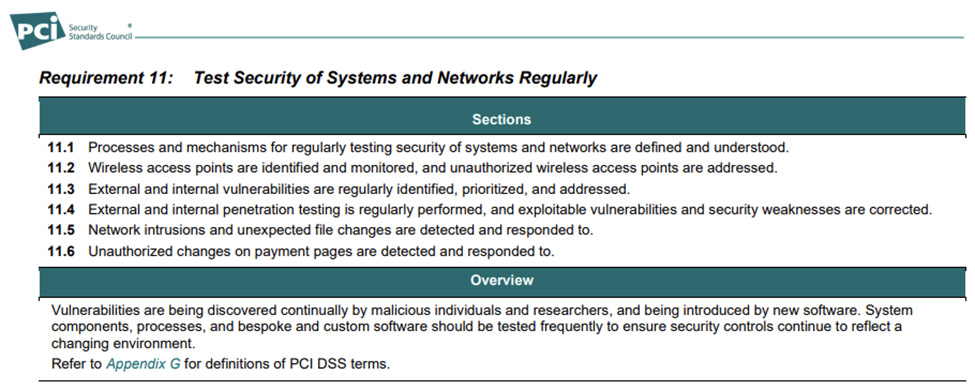
PCI DSS penetration testing must be performed on an organisation’s complete cardholder data environment (CDE) and includes any systems which may impact the security of the CDE.
A PCI pentest helps to identify unsafe system and network configurations, known or unknown hardware or software flaws, rogue wireless networks, improper access controls and operational weaknesses in process-based or technical countermeasures.
Internal and External Network Penetration and Segmentation Testing: Auditors using manual and semi-automated tools will evaluate the security posture of the tested network using the proven testing methodology to potentially compromise servers, endpoints, web applications, optionally wireless networks and other potential points of exposure.
A security assessment is performed with full respect to the customer business and is followed by the clear communication rules, so the risk of service interruption is minimal.
External security testing is conducted from outside the organization’s security perimeter. This offers the ability to view the environment’s security posture as it appears outside the security perimeter—usually as seen from the Internet—with the goal of revealing vulnerabilities that could be exploited by an external attacker.
External testing often begins with reconnaissance techniques that search public registration data, Domain Name System (DNS) server information, newsgroup postings, and other publicly available information to collect information (e.g., system names, Internet Protocol [IP] addresses, operating systems, technical points of contact) that may help the assessor to identify vulnerabilities. Next, enumeration begins by using network discovery and scanning techniques to determine external hosts and listening services. Since perimeter defenses such as firewalls, routers, and access control lists often limit the types of traffic allowed into the internal network, assessors often use techniques that evade these defenses—just as external attackers would.
For internal security testing, assessors work remotely using VPN access to the internal network and assume the identity of a trusted insider or an attacker who has penetrated the perimeter defenses.
An internal security assessment is preferably delivered using virtual machines based on Kali Linux that should be placed in the tested network and accessible to the auditor. This Kali Linux machine should be accessible by the auditor only over VPN equipped with multiple (virtual) network interfaces assigned to all network segments in the scope of CDE and selected 2 non-CDE networks. The placement of the Kali Linux machine is considered temporal and is not included in the security evaluation.
This includes platforms like Amazon Web Services, Microsoft Azure and Google Cloud Platform.
We are using various mainstream, Industry-accepted penetration testing standards and methodologies like:
- NIST 800-115 Technical Guide to Information Security Testing and Assessment
- OWASP Web Security Testing Guide
- OWASP Application Security Verification Standard
- OWASP Mobile Application Security Verification Standard
- The Open Source Security Testing Methodology Manual
A typical test scenario consists of the following steps:
Preliminary analysis of the test system/components
testing and vulnerability analysis
verification of vulnerability – controlled attacks
assess the effectiveness of risk
communicate the results of the tests (detailed report)
Our Penetration Testing Team consist of experienced (between 10+ and 15+ years of experience) senior members that hold widely recognized certificates ( such as CISSP, CEH, OSCP - Offensive Security Certified Professional, OSCE - Offensive Security Certified Expert, OSEE - Offensive Security Exploitation Expert) and a proven list of delivered projects to the customers from various sectors like banking industry, governments, globally recognized payment service processors, crypto currency exchange platforms, gambling and online gaming platforms.
Pen-testers has a proven list of the delivered projects to the large organizations, globally scaled solutions and platforms that process sensitive personal and financial information.
Penetration testers are organizationally separate from the management and maintenance team of the tested target systems as well acts as an independent team from the Qualified Security Assessors - such separation ensures that obtained results are collected and analyzed as independent parties.